Securing IT Infrastructure with a Three-Layer Firewall Approach: A Guide to Multi-Vendor Layered Defense
Build a robust IT infrastructure to protect against external threats, internal breaches, and endpoint/cloud vulnerabilities using a three-layer firewall system.
CYBERSECURITY
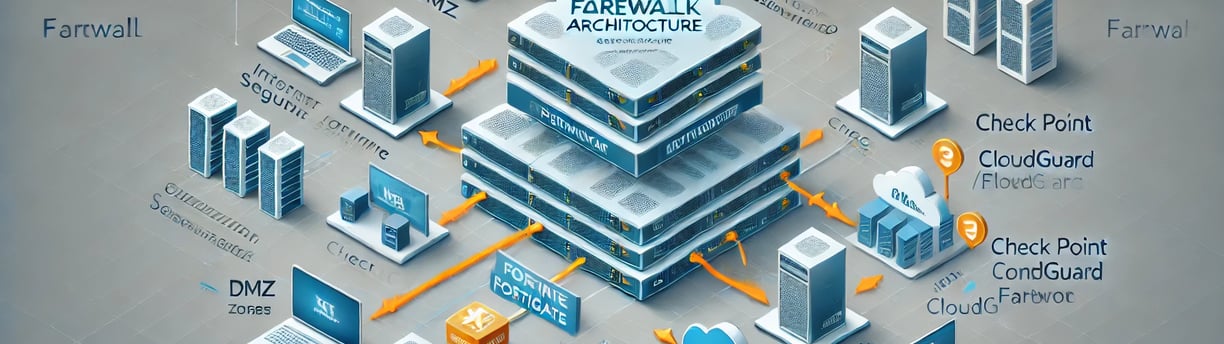
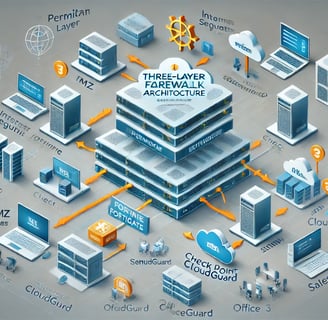
Protecting IT infrastructure is a critical priority for organizations of all sizes. The rising complexity of cyber threats necessitates robust and adaptable security measures. One such strategy is implementing a three-layer firewall architecture, which combines multiple firewalls from different manufacturers. This approach not only enhances security but also reduces the risk of zero-day vulnerabilities.
In this blog, we’ll explore:
The purpose of a three-layer firewall setup.
The advantages of using firewalls from different manufacturers.
The benefits of a layered defense strategy.
Understanding the Three-Layer Firewall Architecture
The three-layer firewall strategy is based on segmenting your network into different zones of trust, each protected by a firewall. Each layer has a distinct purpose:
Perimeter Firewall:
Purpose: Protects the outer boundary of your network by blocking unauthorized traffic and filtering harmful data packets.
Key Features: Basic intrusion prevention, DDoS mitigation, and access control.
Example: Fortinet or Palo Alto Networks firewalls are often used for their high-performance perimeter security.
Internal Segmentation Firewall (ISFW):
Purpose: Separates internal networks into smaller, secure zones to prevent lateral movement of threats.
Key Features: Micro-segmentation, application control, and user-based policies.
Example: Cisco Secure Firewall excels at granular control within internal networks.
Endpoint/Cloud Edge Firewall:
Purpose: Protects critical applications, cloud resources, or sensitive data by focusing on endpoint security.
Key Features: Zero Trust Network Access (ZTNA), advanced threat intelligence, and real-time monitoring.
Example: Check Point or Sophos firewalls are well-suited for securing endpoints and cloud services.
Advantages of Using Different Manufacturers
Using firewalls from different vendors across layers offers several benefits:
Minimized Risk of Zero-Day Vulnerabilities:
Zero-day exploits often target specific vulnerabilities in a particular firewall. By deploying firewalls from different manufacturers, you reduce the risk of a single exploit compromising all layers.
Diversified Security Features:
Each vendor brings unique strengths to the table, such as better threat intelligence, faster packet processing, or advanced artificial intelligence (AI) capabilities.
Enhanced Resilience:
If a flaw is discovered in one firewall, the others remain unaffected, maintaining the integrity of your overall security.
Vendor Independence:
Avoiding reliance on a single vendor eliminates supply chain risks and allows greater flexibility in adapting to emerging threats.
Benefits of a Layered Defense Approach
Comprehensive Threat Mitigation:
Each layer addresses specific attack vectors, ensuring no single threat can penetrate the entire system.
Improved Incident Containment:
If a breach occurs, segmentation ensures that it is isolated within a specific zone, preventing further spread.
Regulatory Compliance:
Layered defenses with firewalls from diverse manufacturers help meet stringent compliance requirements, such as GDPR or HIPAA, by providing robust audit trails and enhanced data protection.
Scalability:
As your organization grows, additional firewalls or zones can be integrated without disrupting the existing architecture.
Proactive Defense Against APTs (Advanced Persistent Threats):
Layered security creates multiple obstacles for persistent attackers, significantly delaying or deterring their success.
Best Practices for Deploying a Three-Layer Firewall System
Careful Vendor Selection:
Choose manufacturers with complementary features rather than overlapping capabilities. For instance, pair Fortinet's high-speed filtering with Cisco's granular controls and Check Point's endpoint protection.
Regular Updates and Patching:
Ensure that all firewalls are kept up to date with the latest patches to guard against known vulnerabilities.
Integrated Monitoring:
Use a centralized security information and event management (SIEM) system to monitor all firewalls, ensuring seamless threat detection across layers.
Employee Training:
Educate IT staff on managing multi-vendor environments and responding to potential incidents.
Simulated Attacks:
Regularly test your defenses using ethical hacking techniques to uncover weak spots.
Conclusion
A three-layer firewall architecture is an essential strategy for modern IT security. By combining firewalls from different manufacturers, you create a robust, layered defense that minimizes vulnerabilities, enhances resilience, and ensures comprehensive protection against sophisticated cyber threats.
Investing in this multi-faceted approach not only safeguards your organization but also positions it to respond proactively to an ever-evolving threat landscape.
#Cybersecurity #networksecurity #firewall #defenseindepth #layerapproach #infosec #zerodayapproach
